Researchers Uncover 'LLMjacking' Scheme Targeting Cloud-Hosted AI Models
13.05.2024
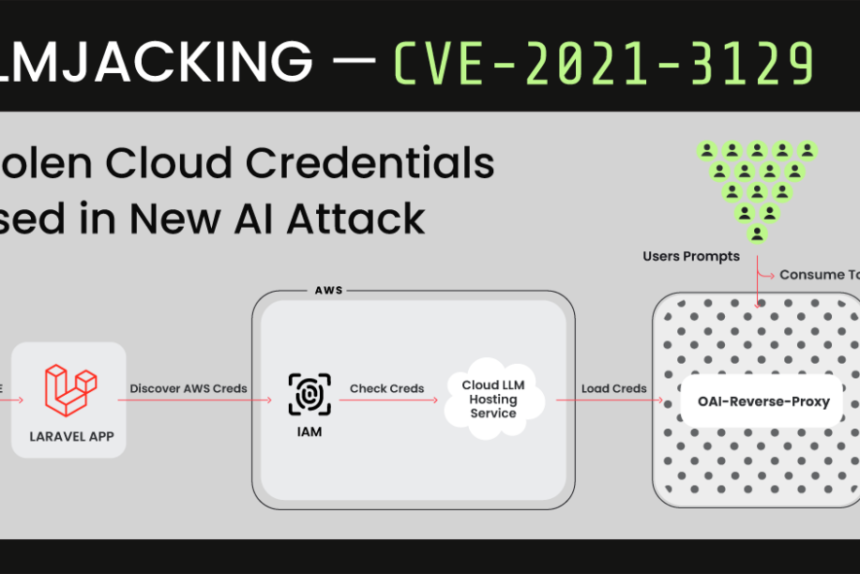
Cybersecurity researchers have uncovered a new attack targeting cloud-hosted large language model (LLM) services, leveraging stolen cloud credentials with the aim of selling access to other threat actors. Dubbed LLMjacking by the Sysdig Threat Research Team, the attack involves breaching systems running vulnerable versions of the Laravel Framework (e.g., CVE-2021-3129) to obtain initial access. Once inside, attackers exfiltrate cloud credentials and attempt to access local LLM models hosted by cloud providers. In a recent incident, a local Claude (v2/v3) LLM model from Anthropic was targeted.
The attackers utilize various tools, including an open-source Python script that validates keys for offerings from Anthropic, AWS Bedrock, Google Cloud Vertex AI, Mistral, and OpenAI. During the validation phase, no legitimate LLM queries are made; instead, the focus is on determining the capabilities of the stolen credentials and any associated quotas. Additionally, the attackers employ an open-source tool called oai-reverse-proxy, functioning as a reverse proxy server for LLM APIs, potentially enabling them to monetize their access without exposing the credentials directly.
To evade detection, the attackers query logging settings, aiming to conceal their activity when using compromised credentials. This approach marks a shift from traditional attacks involving prompt injections and model poisoning, allowing attackers to exploit LLM access while the cloud account owner bears the financial burden.
According to Sysdig, such an attack could result in substantial LLM consumption costs, potentially exceeding $46,000 per day for the victim organization. Maximizing quota limits could also disrupt legitimate business operations by preventing the compromised organization from using LLM models effectively.
To mitigate such threats, organizations are advised to implement detailed logging and monitor cloud logs for any suspicious or unauthorized activities. Moreover, robust vulnerability management processes should be in place to prevent initial access to cloud environments.