Beware! YouTube Videos Promoting Cracked Software Distribute Lumma Stealer
09.01.2024
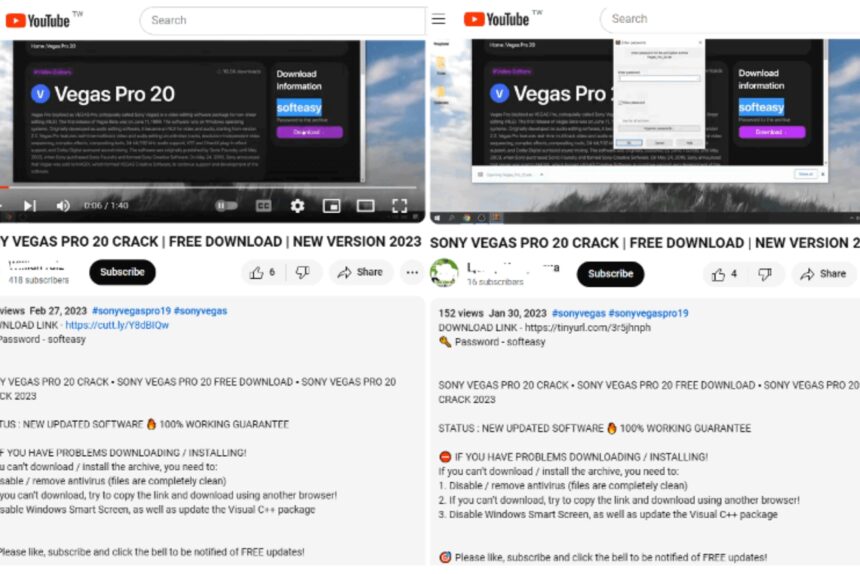
Threat actors are employing a new tactic by utilizing YouTube videos featuring content related to cracked software to entice users into downloading Lumma, an information-stealing malware, according to an analysis by Fortinet FortiGuard Labs researcher Cara Lin. These videos typically showcase content related to cracked applications and provide users with installation guides, often incorporating malicious URLs shortened using services like TinyURL and Cuttly.
This method of using pirated software videos on YouTube as a lure for stealer malware is not unprecedented. Similar attack chains have been observed in the past delivering various types of malware, including stealers, clippers, and crypto miners.
In the recent attack sequence outlined by Fortinet, users seeking cracked versions of legitimate video editing tools, such as Vegas Pro, on YouTube are directed to click on a link in the video’s description. This link leads to the download of a fake installer hosted on MediaFire. Once unpacked, the ZIP installer includes a Windows shortcut (LNK) posing as a setup file. This shortcut downloads a .NET loader from a GitHub repository, subsequently loading the Lumma stealer payload after conducting anti-virtual machine and anti-debugging checks.
Lumma Stealer, written in C and available for purchase on underground forums since late 2022, has the capability to harvest and transmit sensitive data to a server controlled by the threat actor.
This development coincides with Bitdefender’s warning of stream-jacking attacks on YouTube, where cybercriminals exploit high-profile accounts through phishing attacks deploying the RedLine Stealer malware. This allows them to extract credentials and session cookies, ultimately promoting various crypto scams.
Additionally, an 11-month-old AsyncRAT campaign has been discovered, employing phishing lures to download an obfuscated JavaScript file. This file is then utilized to deploy a remote access trojan.