TP-Link Gaming Router Vulnerability Exposes Users to Remote Code Attacks
A critical security vulnerability has been identified in the TP-Link Archer C5400X gaming router, potentially allowing remote code execution by sending specially crafted requests.
View Case Studie DetailsZoom Adopts NIST-Approved Post-Quantum End-to-End Encryption for Meetings
Zoom, a popular enterprise services provider, has announced the rollout of post-quantum end-to-end encryption (E2EE) for Zoom Meetings, with support for Zoom Phone and Zoom Rooms expected in the future.
View Case Studie DetailsApple and Google Launch Cross-Platform Feature to Detect Unwanted Bluetooth Tracking Devices
Apple and Google announced the launch of a new feature on Monday, which notifies users on both iOS and Android platforms if a Bluetooth tracking device is being used to monitor them without their consent.
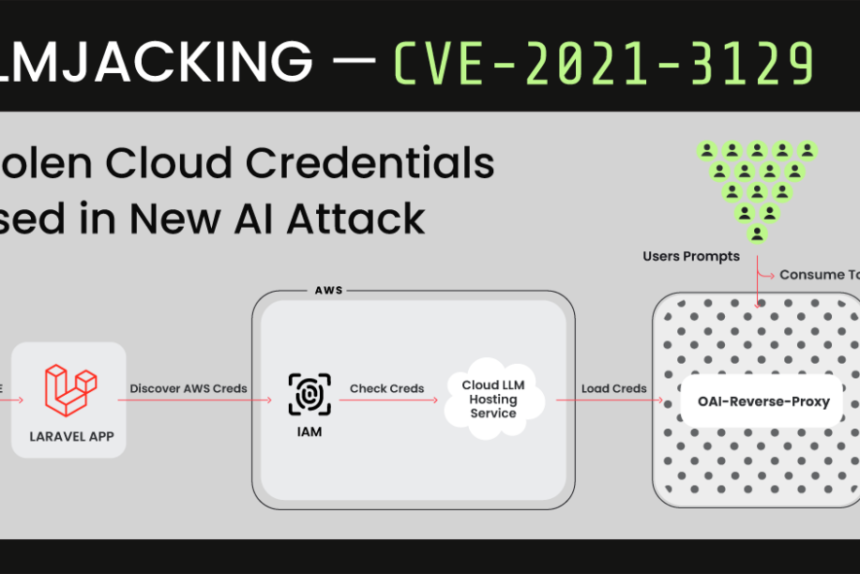
View Case Studie DetailsResearchers Uncover ‘LLMjacking’ Scheme Targeting Cloud-Hosted AI Models
Cybersecurity researchers have uncovered a new attack targeting cloud-hosted large language model (LLM) services, leveraging stolen cloud credentials with the aim of selling access to other threat actors.
View Case Studie Details